Cetbix CLEH (Computer and Linux Environment Hardware) Compliance is built to scale from small to large environments by using intelligent and efficient algorithms, modern hardware, and software modularity. Components can be spread across different servers to enhance performance. Cetbix CLEH gathers all the important yet hard-to-find details about the hardware in a computer system. This type of data is valuable to individuals and large-scale environments with over 100,000 of monitored devices.
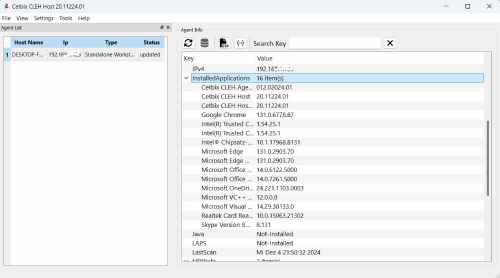
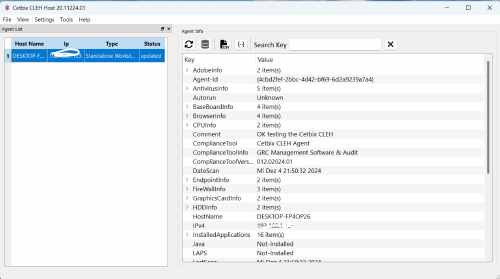
CLEH extracts details of all components of the Windows PC and Linux Systems, shows installed software, and computer's hardware. It is suitable for users searching for driver updates, computer manufacturers, system integrators, and technical experts.
CLEH supports 32-bit and 64-bit versions of Windows and Linux machines. Server operating systems, including Windows Home Server, are also supported.
CLEH supports 32-bit and 64-bit versions of Windows and Linux machines. Server operating systems, including Windows Home Server, are also supported.
CLEH supports 32CLEH supports 32-bit and 64-bit versions of Windows and Linux machines. Server operating systems, including Windows Home Server, are also supported.-bit and 64-bit versions of Windows and Linux machines. Server operating systems, including Windows Home Server, are also supported.
CLEH supports 32-bit and 64-bit versions of Windows and Linux machines. Server operating systems, including Windows Home Server, are also supported.
Scalability: The Cetbix CLEH system is designed to scale efficiently, using advanced algorithms and the latest technology. Thanks to its modularity, components can be deployed on multiple servers, improving performance and reliability.
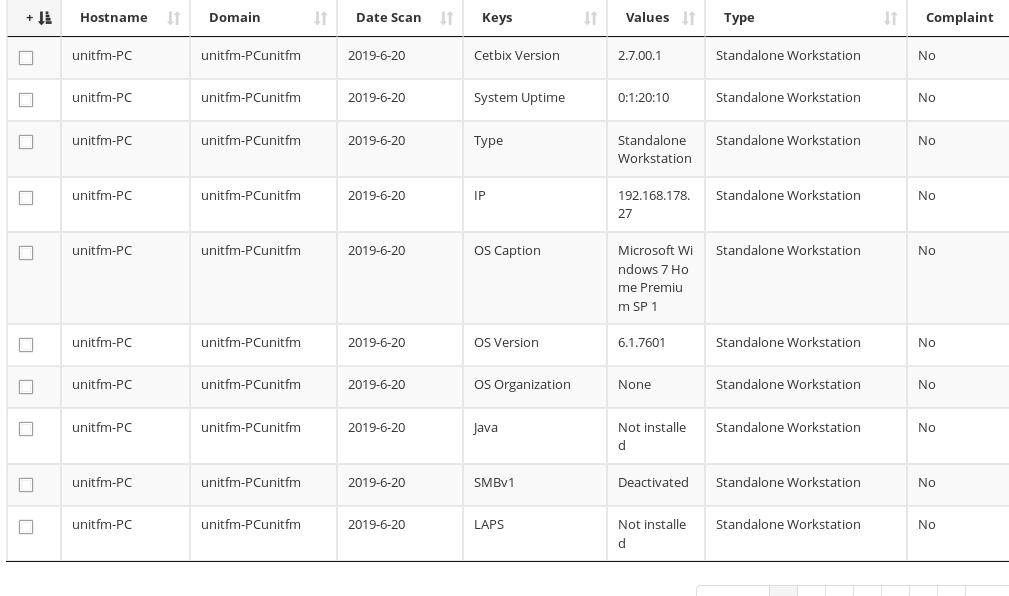
Data collection: Cetbix CLEH specializes in collecting comprehensive information about computer hardware components. It collects data from both Windows and Linux operating systems, providing insight into installed software and hardware configurations. This capability is very useful for consumers who need driver updates as well as for computer manufacturers, system integrators and technical specialists.
Compatibility: The Cetbix CLEH software supports both 32-bit and 64-bit versions of Windows and Linux, including server operating systems such as Microsoft Home Server.
Cetbix CLEH is suitable for a range of users, e.g:
Cetbix CLEH increases system performance through several key mechanisms:
Algorithms with intelligence and modular design
Efficient algorithms: Cetbix CLEH uses intelligent algorithms that maximize processing and resource allocation, contributing to the efficient management of workloads in various computing environments.
Modularity: Cetbix CLEH architecture allows components to be distributed among several servers. This distribution increases reliability because the failure of one component does not put the entire system at risk, as well as improving performance through load balancing.
In-depth data collection
Detailed monitoring: CLEH collects extensive data on software and hardware configurations, enabling users to identify performance problems and improve efficiency. It helps make informed decisions about maintenance and upgrades by providing information about installed hardware and software components.
Driver updates: The system helps users locate needed driver updates, which can greatly increase hardware component performance and overall system efficiency.
Scalability
Flexibility in response to user needs: CLEH is built to scale effectively in both small and large environments. The system can easily grow by adding new servers or upgrading current hardware in response to increased user demand, avoiding overload and maintaining high levels of performance3. For companies with varying or rapidly growing workloads, this scalability is essential.
Resource management and load balancing
Load distribution: CLEH divides user requests among several servers using load balancing strategies. This ensures that response times remain fast even during periods of high demand, preventing a single server from acting as a bottleneck.
Cache utilization: The system can use caching to speed up operations and reduce recovery times for frequently requested resources.
In conclusion, Cetbix CLEH improves system performance through resource management techniques, scalability, in-depth monitoring functions, and intelligent design. Together, these features ensure a responsive and effective computing environment for a range of operational needs.
Cetbix CLEH improves system performance in several ways:
Scalable architecture: the system is designed to scale from small to large environments through the use of state-of-the-art hardware and sophisticated algorithms. Its scalability makes it suitable for organizations of any size, as it can efficiently monitor over 100,000 of devices without sacrificing speed.
Modular design: CLEH's modular architecture allows components to be distributed across multiple servers. This distribution increases the overall performance of the system through load balancing and resource optimization.
Comprehensive hardware insights: CLEH helps users find potential bottlenecks and optimize settings by compiling comprehensive data on hardware elements such as CPU, memory and storage. This information is essential for maintaining peak performance and can help guide maintenance or upgrade decisions.
Cross-platform support: CLEH supports both Windows and Linux platforms, organizations can easily deploy it in a variety of contexts. This adaptability allows each system to be monitored efficiently, improving overall performance management.
Cetbix CLEH uses a number of effective algorithms that improve its performance and scalability in monitoring information systems. The following are the essential elements that improve the efficiency of these algorithms.
Intelligent Algorithms: The algorithms are crafted to adeptly collect and analyze data from a variety of hardware components and software environments. This functionality facilitates the rapid identification of system performance metrics and potential issues, thereby optimizing the monitoring process.
Scalability: The algorithms within the system are designed to scale efficiently from small configurations to extensive environments. This capability ensures that even in situations involving over 100,000 of monitored devices, performance remains optimal without significant decline, enabling organizations to expand without outpacing their monitoring solutions.
Modular Architecture: By adopting a modular design, Cetbix CLEH can distribute its components across multiple servers. This approach not only improves performance but also enables parallel data processing, which is essential for sustaining efficiency in large-scale operations.
Cross-Platform Compatibility: The algorithms are designed to function seamlessly on both 32-bit and 64-bit systems, compatible with Windows and Linux platforms. This adaptability guarantees that monitoring capabilities remain uniform and effective, irrespective of the operating system in use, thereby enhancing the tool's utility across a wide range of IT environments.
These attributes collectively ensure that Cetbix CLEH operates effectively, delivering thorough system monitoring while accommodating the requirements of different organizational sizes and structures.

Cetbix CLEH utilizes a variety of strong encryption techniques to safeguard data both during transmission and while stored.
Below are the primary encryption strategies implemented by Cetbix CLEH:
Transport Layer Security (TLS): The Cetbix CLEH employs TLS to secure data during transmission, guaranteeing that any information exchanged over the network is protected against interception. This protocol is well-regarded for its ability to secure communications between clients and servers, establishing it as a preferred option for safe data transfer.
Encryption at Rest: Every piece of data housed within the Cetbix system is encrypted to safeguard sensitive information from unauthorized access. Consequently, even if there is a breach of physical access to the storage system, the data remains inaccessible without the necessary decryption keys.
Asymmetric and Symmetric Encryption: The Cetbix CLEH algorithms utilize a blend of asymmetric encryption for secure key exchange and symmetric encryption for effective data encryption.
Compliance with Data Protection Regulations: Cetbix CLEH complies with data protection regulations that typically require robust encryption methods. This adherence guarantees the secure management of sensitive personal and organizational information throughout its entire lifecycle.
TLS (Transport Layer Security) greatly improves the security of data transmission in Cetbix CLEH by employing several essential mechanisms.
Data Encryption in Transit: Cebix CLEH employs TLS to secure the data transmitted between the client and server, guaranteeing that intercepted data packets remain inaccessible to unauthorized individuals. This encryption is vital for safeguarding sensitive information against eavesdropping and man-in-the-middle attacks, where an adversary might manipulate the communication between two parties.
Authentication Mechanism: TLS offers Cebix CLEH a method for verifying the server's identity through the use of digital certificates. In the TLS handshake, the server presents its certificate, which includes its public key and is endorsed by a recognized Certificate Authority (CA). The client checks this certificate prior to establishing a secure connection, ensuring that it is engaging with the correct server rather than a fraudulent one.
Integrity Verification: To confirm that the data has not been altered during transmission, Cebix CLEH guarantees that the received data matches what was originally sent, thereby preserving data integrity. Should any discrepancies be identified, the connection can be terminated to prevent the processing of compromised data.
Simplified Handshake Process: Cetbix employs TLS 1.3 to enhance the handshake procedure, thereby minimizing latency and boosting performance while upholding strong security measures. This refinement facilitates the rapid establishment of secure connections without compromising security integrity.


The following is a comparative analysis based on essential characteristics.
| Feature | Cetbix CLEH | Other Monitoring Solutions |
|---|---|---|
| Scalability | Built to scale from small to large environments using intelligent algorithms and modern hardware, supporting over 100,000 of devices efficiently | Many solutions also offer scalability, but performance may degrade with high device counts unless specifically designed for it. |
| Cross-Platform Support | Supports both 32-bit and 64-bit versions of Windows and Linux, including server operating systems like Windows Home Server | Some competitors may focus on specific platforms, limiting cross-platform compatibility. |
| Modular Architecture | Features a modular design that allows components to be distributed across different servers, enhancing performance and flexibility | Other solutions may lack this level of modularity, potentially leading to bottlenecks in data processing. |
| Comprehensive Data Collection | Gathers detailed information about hardware components and installed software, making it suitable for diverse environments | Many monitoring tools provide basic metrics but may not offer the depth of hardware details that Cetbix CLEH does. |
| Real-Time Monitoring | Offers real-time insights into system performance and health, enabling quick identification of issues | Most solutions provide real-time monitoring; however, the effectiveness can vary based on the underlying architecture. |
| User-Friendliness | Designed with an intuitive interface that simplifies navigation for users at all levels | User experience varies widely; some tools may have steep learning curves or complex interfaces. |
| Integration Capabilities | Can integrate with various third-party solutions, enhancing its utility within existing IT ecosystems | Many tools offer integration, but the extent and ease of integration can differ significantly. |
| Security Features | Implements strong encryption methods for data protection during transmission (TLS) and at rest | Security measures vary; some may not provide end-to-end encryption or robust authentication methods. |
| Cost Structure | Offers flexible licensing options suitable for different business sizes and needs | Pricing models vary widely; some may be less flexible or more costly depending on feature sets. |
Cetbix CLEH comes with an API that enables data to move seamlessly to the Cetbix Monitoring system where data is automatically evaluated and compared to your organizational requirements. This feature helps managers to have a broader view of their system security.