Departments may have kept their data silos in the form of Excel files or Access databases, which pose additional challenges when it comes to integrating that data into a data mart or data warehouse. Only when you have a complete 360° data inventory can you accurately assess your BI roadmap and implementation strategies.
Inventorizing organization assets using the Cetbix AI enhance comprehensive internal interviews.
The Cetbix AI provides an appropriate set of procedures for information labeling by following the information classification scheme adopted by the organization. This procedure covers information and its related assets in physical and electronic formats.
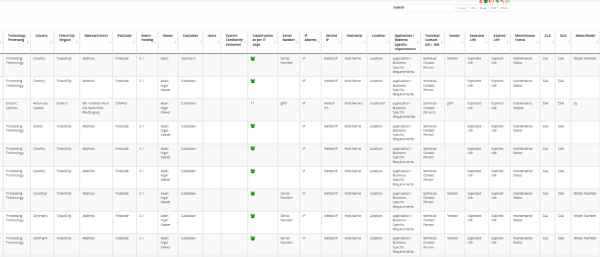
Processing activities internally
As a CISO, CIO, or Security Manager, you are to maintain a record of all your organization’s processing activities internally and to make them available to supervisory authorities upon request.

Traditional Data Inventories
Cetbix Asset Classification covers both personal data and general data. Organizations are overwhelmed with a lot of information. Addressing these challenges manually or repository by repository is time-consuming and error-prone. There is a better way – and it starts with a data inventory.

Advantage of Cetbix Inventory
Cetbix inventory enables organizations to create a data inventory for the prioritization of efforts, resources, and assessing risks.